High-Impact Vulnerabilites In Multiple USB Network Servers
Within the scope of a recent penetration test and through individual research effort, HiSolutions‘ security consultants discovered multiple previously unknown high-impact vulnerabilities in USB network server firmwares (see individual issues for the CVE IDs). Devices of multiple vendors were affected by similar vulnerabilities. HiSolutions responsibly disclosed the vulnerabilities to the vendors and additionally provided feedback on the implemented patches.
Background Information
USB network servers or USB network MTP and printer servers are devices that can be used to make USB devices accessible to multiple users via the network. Users install a software on their client and can then access USB devices without the need to physically plug the device into the local system. If devices are used by multiple users the devices do not have to be transfered between different systems each time the user changes. Use cases include shared USB network drives, USB Printers, or USB license dongles that can be used by authenticated users on the local network. All of the investigated devices were provided with an individual client software that runs on the local systems. All systems also exposed a web server that could be used to make administrative changes to the system.
The Vulnerabilities
HiSolutions consultants discovered four noteable vulnerabilities in each of the investigated devices.
The devices were:
- TP-Link TL-PS310U (version v2.000, fixed in 2.079.000.t0210)
- Digitus da-70254 (version 2.073.000.E0008)
- Lindy No. 42633 (version v.2.078.000)
- one other reviewed device of an (at this time) undisclosed vendor
Exposure of the Administrative Password Over Network Broadcast
The following CVE IDs were issued for this vulnerability: CVE-2020-15054 (TP-Link), CVE-2020-15058 (Lindy), CVE-2020-15062 (Digitus).
The USB network servers send the password of the local administrator account repeatedly and without request across the local Network via UDP broadcast. Every system on that network can read the password from these unencrypted broadcasts. The password is sent in UDP packets to the broadcast address 255.255.255.255 as can be seen in the following packet capture:
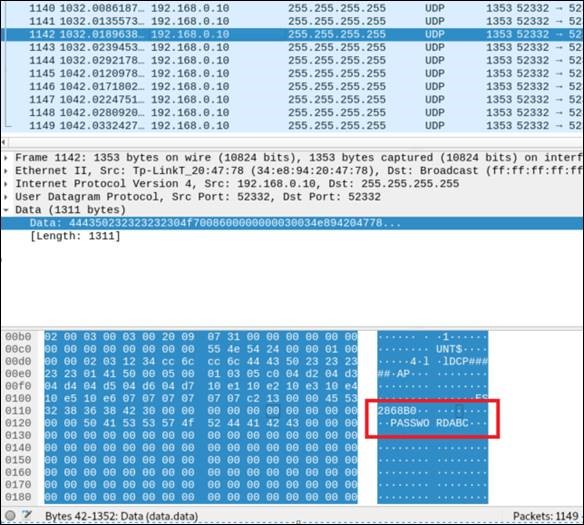

Figure 1: UDP broadcast of the administrative password „PASSWORDABC“.
All systems in the local network receive the administrative password. In theory, the password is then used to locally check against the password entered by the client on the local system. In practice, an attacker can easily retrieve the password from the UDP broadcast messages and thus
circumvent the access restrictions to the administrative interface. The attacker then can use all functions provided by the USB network server, including restricted ones. If the password is reused (which is strongly discouraged but often the case) this design error could give an attacker access to other systems that use the same password.
Authentication Bypass in Web Administration Interface
The following CVE IDs were issued for this vulnerability: CVE-2020-15055 (TP-Link), CVE-2020-15059 (Lindy), CVE-2020-15063 (Digitus).
In some cases the password authentication requirement in the web interface can be bypassed when the password parameter is removed from the request. This enables an unauthenticated user to access privileged functions on the interface.
As an example, the following request will change the server name, a functionality that would normally only be available if the configured password was provided:
POST /csystem33.htm HTTP/1.1 Host: 192.168.0.10 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: http://192.168.0.10/csystem33.htm Content-Type: application/x-www-form-urlencoded Content-Length: 53 Connection: close Upgrade-Insecure-Requests: 1
%24A0%24=New+Name+No+Password&%24B2%24=38&%24B3%24=39
As is visible in the request, no password is provided and the corresponding Parameter is removed entirely. Without the password parameter the authentication does not fail, but instead the server simply implies that no password was set, thus allowing the operation without any user authentication.
Because of that, unauthenticated users can access administrative functions on the system without knowledge of the administrative password, therefore bypassing the authentication. This effectively disables the access control for the entire administrative interface.
Persistent Cross-Site Scripting
The following CVE IDs were issued for this vulnerability: CVE-2020-15056 (TP-Link), CVE-2020-15060 (Lindy), CVE-2020-15064 (Digitus).
The parameter for the server name is vulnerable to a stored Cross-Site Scripting (XSS) attack. This results in the possibility for an attacker to execute JavaScript code in the context of the victims browser.
If the corresponding request is sent to the server, the server name gets embedded into the JavaScript file unfiltered and unescaped:
var myServer = new Server();
myServer.model = '';
myServer.manuf = '';
myServer.name = 'TestName';alert('Successful XSS');//';
myServer.hw = 'V. 2.000';
//myServer.tempFW = '2.255.255';
tempFWVersion = '';
myServer.fw = tempFWVersion.substring(0,1) + '.' +
tempFWVersion.substring(1,3);
myServer.mac = '34:e8:94:20:47:78';
The vulnerability allows attackers to execute JavaScript code in the context of the browser of the victim by manipulating the stored server name. Attackers in the local network could insert a custom script that is loaded each time an administrator visits the web administration interface. They can thereby gain persistent access to the web interface and attack other systems in the local network through the browser of the victim.
Normally, administrative access to the web interface would be needed to exploit this vulnerability, which would lower the impact. In combination with other vulnerabilities (like the authentication bypass) this exploit works for all users with access to the system.
Denial of Service
The following CVE IDs were issued for this vulnerability: CVE-2020-15057 (TP-Link), CVE-2020-15061 (Lindy), CVE-2020-15065 (Digitus).
Users can crash the USB network servers by sending long input values. For some lengths, the servers hang or act unexpectedly. while longer input values (e.g. 1103 characters) will crash them entirely. A reboot or sometimes reset of the device is needed to clear the issue.
After receiving too long input values the system no longer responds to network requests. The UDP broadcasts show that when setting a long server name other variables were most likely overwritten:


Figure 2: Buffer overflow from the server name (top: normal, bottom: after attack)
An attacker can use the buffer overflow vulnerability to impact the availability of the server. The shown behaviour indicates that the buffer overflow could also be used to execute functions or code on the system. This possibility was not investigated during the project.
Remediation
The vendors TP-Link and Lindy provided an updated firmware that fixes the vulnerabilities.
When using a device for which no patch is available, make sure that the chosen password is not reused on any other system or application.
Access to the devices could also be restricted on network level to limit the possibility of an attacker accessing the web interface or sniffing the broadcast traffic.
Responsible Disclosure Timeline
The vulnerabilities were reported to each of the vendors via e-mail. It was made clear that HiSolutions will follow defined responsible disclosure policy and aims to release information about the vulnerabilities in coordination with the vendor.
Each but one vendor reacted to the initial contact and in the following dialogue was provided with additional information on the vulnerabilities.
The vendors named in this advisory provided patches to mitigate the security issues. Hisolutions tested the patches for their effectiveness until the discovered vulnerabilities were closed and follow-up problems solved adequately.