TL;DR (Teamwire users): Multiple vulnerabilities have been found in Teamwire which allow malicious users to execute commands on victim’s computers. Upgrade Teamwire to the newest version (at least v2.5.0 as of Jan 21, 2021) as soon as possible to fix the vulnerabilities.
TL;DR (Technical): Cross-site-scripting and HTML injections are common vulnerabilities in web applications. If a desktop application, like the Teamwire Windows client, builds on a web engine which is vulnerable to these issues, this can result in remote code execution on the client systems.
Vulnerability Summary
A HiSolutions researcher discovered that code could be executed in other users clients if a crafted message was shown in their search results (CVE-2024-24275). Another vulnerability in the handling of pasted text (CVE-2024-24278) and potential issues that allowed for the injection of sanitized HTML-elements (CVE-2024-24276) were found and reported to Teamwire.
Teamwire replied back that the issues were independently found in an internal security audit a few weeks before and released a new Teamwire version within a day.
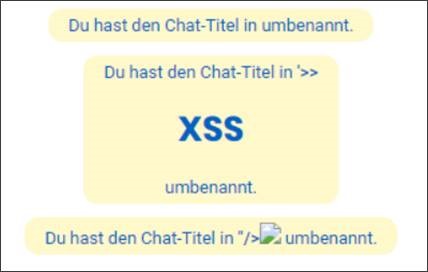
When HiSolutions reviewed this new version, it was discovered that only a part of the reported vulnerabilities were fixed. Furthermore, the previously identified RCE (CVE-2024-24275) vulnerability could be exploited again in this version, just slightly different this time. In the new version, code was executed when an attacker created a group with a specially crafted name and invited victims to the group as well as in any other places where the group name was shown (e.g. search results or group directory).
Background
Teamwire uses different technologies for their Windows desktop client that contained the below mentioned vulnerabilities. The client is based on NW.js. As written in our last article about a different set of Teamwire vulnerabilities:
NW.js is a technology that combines the browser engine WebKit with the JavaScript framework Node.js, and is often used to create cross-platform applications. This combination enables users to call Node.js functions directly from the DOM of the embedded Chromium browser.
The application itself then uses, among other technologies, AngularJS for client side JavaScript functionality.
Vulnerability Details
Desktop client RCE through search results (CVE-2024-24275)
In versions below 2.3.0 of the Teamwire Windows desktop client, when a message that contained HTML code was shown inside the search results, this HTML code was embedded inside the client without any sanitization or encoding. Any included HTML elements were rendered and JavaScript code executed, allowing for arbitrary code execution. This issue affected both the chat and the global search function. Through NodeJS functions, commands could be executed directly on the operating system of the victim.
If the attacker created an arbitrary group, posted messages similar to:
<img src=x onerror="const spawn=require('child_process').spawn;spawn('cmd.exe',['/c','calc.exe']);console.log(1);//Something searchword">
and invited a victim, the payload was planted inside the client application. When a victim then did a search (inside the chat or global search) for a word matching any of the additionally supplied words (see text in red in payload), the code was executed on the client system. For demonstration purposes, the program calc.exe was opened but any actions inside the application or on the system would have been possible.
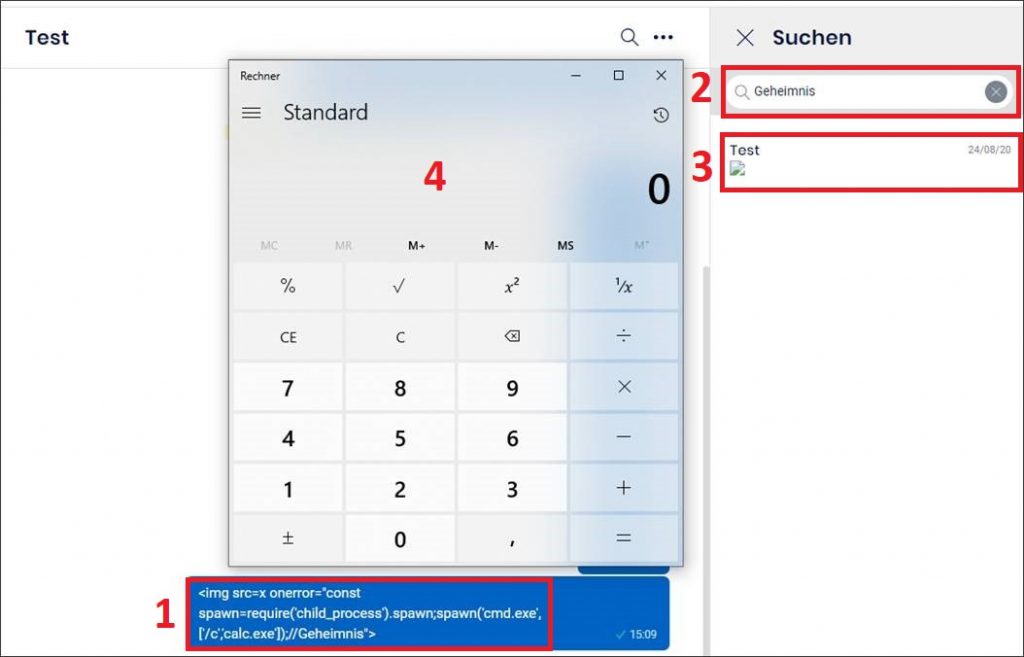
The underlying reason for this behaviour seemed to be the function that normally provided the highlighting of the search words (angular.module("Teamwire.filters").filter("highlight",…). This function did not sanitize, filter or encode the messages in the search results before using the AngularJS function trustAsHtml and embedding the result. Any included HTML elements were therefore rendered and any contained JavaScript code executed.
This behaviour affected the versions of the Teamwire Windows desktop client between version numbers 2.0.1 and below 2.3.0. Older versions may be affected as well.
The vulnerability was fixed in version 2.3.0.
However, version 2.3.0 was affected in another way by the following vulnerability.
Desktop client RCE through list names (also tracked under CVE-2024-24275)
In version 2.3.0 of the Teamwire Windows desktop client, group names were embedded inside the client without any sanitization or encoding. Any included HTML elements were rendered and JavaScript code executed in multiple places, allowing for arbitrary code execution. Through NodeJS functions, commands could be executed directly on the operating system of the victim.
If the attacker created a group with the name
<img src=x onerror="const spawn=require('child_process').spawn;spawn('cmd.exe',['/c','calc.exe']);console.log(1);//Something">
and invited the victims, the code was executed on the client systems. For demonstration purposes, the program calc.exe was opened but any actions inside the application or on the system would have been possible.
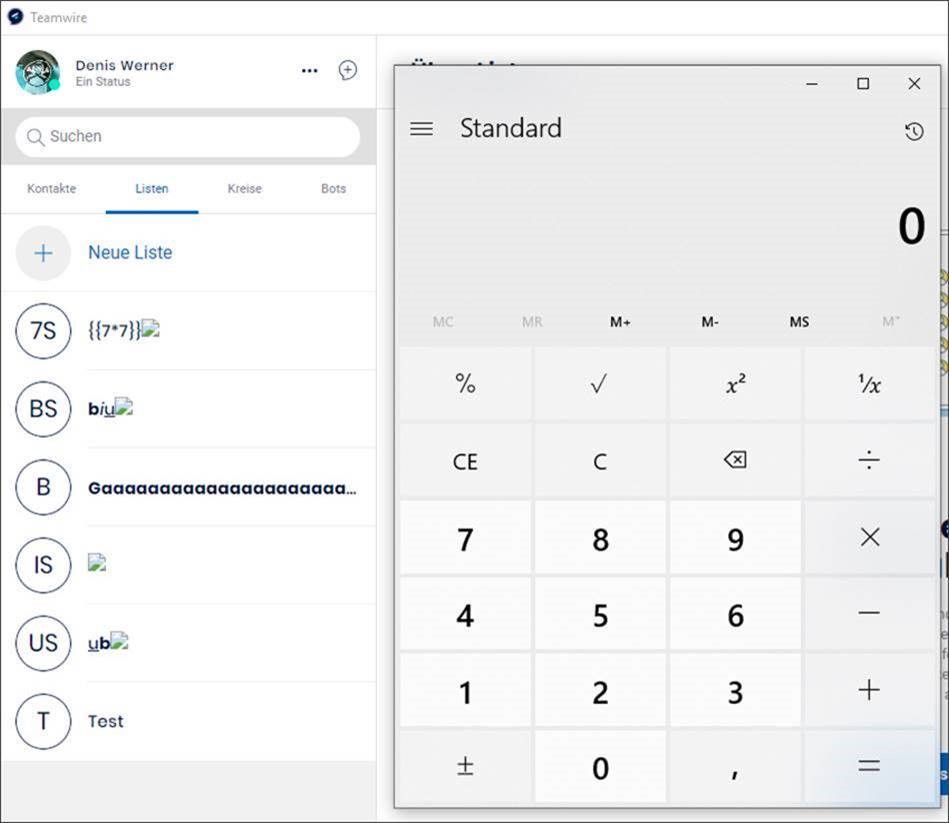
The injected code was executed at least in the following places:
- When a user viewed the tab „Directory“ and then „Lists“ and was added to the malicious group by the attacker
- When a user used the global search and the malicious group name matched the search word
- When a user viewed the members of a group chat that contained the malicious group as a member
- When a user wanted to create a new group chat and the malicious group was an element in the „Lists“ directory
This behaviour affected version 2.3.0 of the Teamwire Windows desktop client. Older versions were not affected.
The vulnerability was fixed in version 2.4.0.
Automatic UNC path resolution in pasted text (CVE-2024-24278)
If a user pasted text into the message area of the Teamwire Windows client and that text matched a UNC path, the Teamwire client automatically tried to connect to the system and proceeded to authenticate via SMB with the current Windows logon credentials. An attacker inside the internal network could use this vulnerability to capture hashed credentials or redirect the user authentication attempt to other systems.
For example: If a user pasted the text „\\192.168.194.133\something\test.docx“ into the message field, the client tried to access the SMB share on the system 192.168.194.133 immediately without showing the pasted text first.
This behaviour would be expected if a client would click on a link or open the path in the Windows explorer. It is however not expected if a user only pastes the text without submitting it or initiating any other action. Especially if a user copies text from a web page, where malicious content could be hidden by CSS, unintended text might be pasted into the application. The pasted content is only shown after the connection to the specified share was already established.
This behaviour affected all versions of the Teamwire Windows desktop clients between version numbers 2.0.1 and 2.4.0. Older versions may be affected as well. A newer version than 2.4.0 may include a fix but was not tested.
Injection of sanitized HTML elements in multiple places (CVE-2024-24276)
At least four instances inside the Teamwire Windows client were identified, where user supplied HTML code was rendered inside the application. The HTML code however, was sanitized by the AngularJS sanitize$ function, which prevented the insertion of malicious JavaScript code. An attacker would need to find a bypass for this function to elevate these issues into remote code exection vulnerabilities.
Without such a bypass, only harmless modifications like manipulation of the application appearance or embedding of external images was possbile.
The four identified instances were:
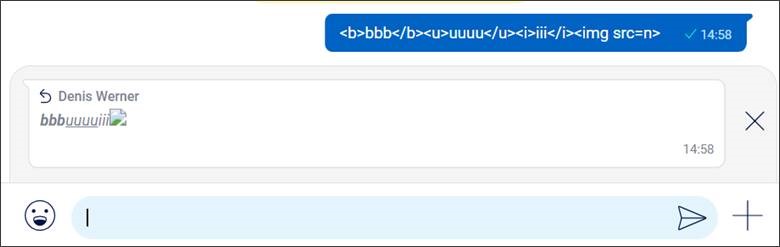
- When an administrator renamed a chat, the new name was sent to all members of the group and the sanitized HTML was rendered

- The message preview when a user answered another message

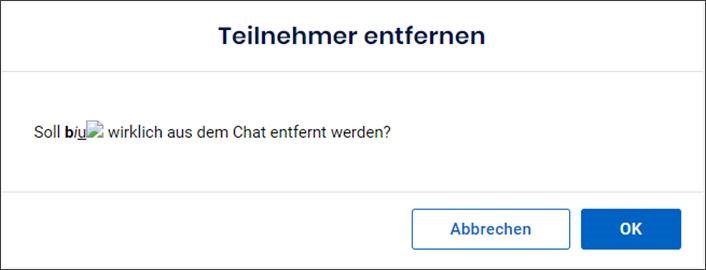
- When a user with a manipulated name was removed from a group

- When an administrator tried to leave a chat that still contained a group of which he was a member
This behaviour affected all versions of the Teamwire Windows desktop clients between version numbers 2.0.1 and 2.2.1. Older versions may be affected as well.
Instances 2 and 4 were fixed in version 2.3.0.
Instances 1 and 3 still exist in 2.3.0 and possibly later versions as well.
Disclosure Timeline
- 25. August 2020 – HiSolutions reaches out to Teamwire to establish secure, encrypted communication via email so that vulnerability details can be sent
- 25. August 2020 – Teamwire provides a contact and the corresponding PGP key
- 25. August 2020 – HiSolutions sends the vulnerability details for the three vulnerabilities CVE-2024-24275, CVE-2024-24276, CVE-2024-24278
- 26. August 2020 – Teamwire responds that the mentioned issues were internally discovered a few weeks before and releases a new Teamwire version 2.3.0 that is supposed to contain the fixes
- 26. August 2020 – HiSolutions tests the new version
- 27. August 2020 – HiSolutions sends the details of the retest and the new vulnerability to the Teamwire contact
- 16. October 2020 – Teamwire publishes version 2.4.0 which includes fixes for some of the vulnerabilities
- 2020/2021 HiSolutions can no longer assess Teamwire and pauses the responsible disclosure process
- 16. January 2024 – HiSolutions publishes the vulnerability details after a sufficient grace period
Credits
The vulnerabilities were found by Denis Werner (HiSolutions AG) who also reviewed the fixes.